Navigation
Tags
attrition: advisory errata archive vendor_fail news charlatan lazlo security_comp_fail going_postal rant box_of_shit movie_review book_review music_review contest buy_shit
twitter: technical_difficulties unsolicited_updates foursquare wefollow musings imdb dmfail
hobbies: critter_of_the_day squirrel guinea_pig stalking
related: osf datalossdb conference osvdb
type: quote screenshot photo video tweet audio question chat link
Links
Tools
-
A Glimpse Into the CISA KEV
On March 27, Elizabeth Cardona and Tod Beardsley gave a presentation at VulnCon 2024 about CISA’s KEV, or ‘Known Exploited Vulnerabilities’ list. This initiative was created as a result of BOD 22-01, which is a ‘Binding Operational Directive’ aimed at reducing the risk due to vulnerabilities that are known to be exploited in the wild, and that may impact federal, executive branch, departments and…
3 days ago -
VulnCon: NVD Symposium, Answers, and More Concerns
Yesterday, at the first inaugural VulnCon, Tanya Brewer from the NVD gave a presentation that was listed on the agenda as “NVD Symposium”. At the talk, her slides began with a header “The National Vulnerability Database: Exploring Opportunities”. However, neither were the primary topic that most people were interested in. Fortunately for the crowd Tanya, the NVD Program Manager for the last four…
Notes: 1 / 3 weeks ago -
The Linux CNA - Red Flags Since 2022
MITRE announced that The Linux Kernel Organization (Kernel.org, hereafter referred to as ‘Linux’) was officially a CNA on February 13, 2024 and via the CVE web site, that their advisories would be posted here. Several prominent members in the industry have already voiced concerns about this including Chompie, Ian Coldwater, Brad Spengler, and Katie Moussouris. All of them, and more, are exactly…
1 month ago -
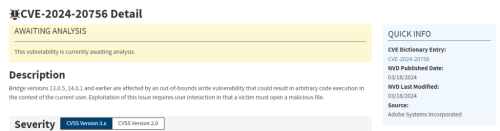
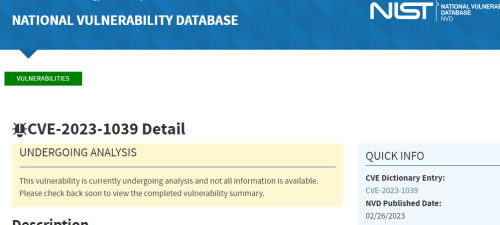
2024 and Some Still Don’t Understand the CVE Ecosystem
[Update: Even before I publish this, I want to keep everything I wrote for now. But I believe this rebuttal is in response to trash written by SpiceWorks and a GPT.]
The world of vulnerability disclosures is growing fast, for a variety of reasons I won’t get into. Suffice it to say my time is limited. So a quick rebuttal to an article on Spiceworks titled “What Are Common Vulnerabilities and…3 months ago -
Puzzling the Community a Bit!
5 months ago -
The Fine Art of Wooden Puzzles
6 months ago -
Concert: Tash Sultana
On Saturday night, I went to my first concert in … a long time, maybe a decade? In fact, someone asked me when the last concert I went to was and it sent me down a rabbit hole because apparently I didn’t start using Google Calendar until much later than I remembered. After digging through emails, prior concert reviews, and a really poor memory, I put together that list. Then I remembered I keep…
Notes: 1 / 7 months ago -
Speaking Ill of the Dead?
Folks in the Information Security (InfoSec) circles are getting old. It is evident from the last few years and seeing those we know, in some capacity, passing on. For many of us still here, we find ourselves battling a world of conditions ranging from the relatively simple high blood pressure, to the more complicated like diabetes. That doesn’t even speak to the separate issues like so many in…
Notes: 1 / 9 months ago -
That Vulnerability is “Trending” … a Redux
A couple weeks ago I published a blog titled “That Vulnerability is ‘Trending’ … So What?“. I didn’t think I would be publishing another on this topic, especially this fast. But I ran into another absurd case of a vulnerability “trending” and figured out why, which is even more ridiculous. I caused this…
A CVE came across one of our feeds that monitors Twitter for mentions of a CVE ID that isn’t…Notes: 5 / 1 year ago -
That Vulnerability is “Trending” … So What?
Yesterday, more than one organization reached out to my company asking why a particular vulnerability wasn’t in VulnDB yet. First, it had been less than 24 hours since publication in CVE/NVD, NVD hasn’t analyzed it as of the time of this blog, and it is in software no significant business would use. It’s part of a pattern of vulnerabilities being disclosed in low-end personal PHP projects, most…
1 year ago -
2022 #MakeHimHurt Challenge - The Results
1 year ago -
Rebuttal? Not really… Comments on Curphey’s Latest Blog
Rebuttal? Not really… Comments on Curphey’s Latest Blog
I went into a LinkedIn post expecting to have to buy a new box of red sharpies to be honest, but I am pleasantly surprised at the conclusions regarding CVE / NVD, which I think are largely accurate. As grim a picture as is painted, they are still a bit too generous. I say that as someone who reads, quite literally, every new CVE published and have for coming up on 20 years. Pretty sure no one at…
1 year ago -
Will the Real 300,000 Stand Up?
Will the Real 300,000 Stand Up?
On September 27, 2022, Flashpoint’s VulnDB hit the 300,000th entry added to the database. Think about that and .. wow. I started the adventure of collecting vulnerabilities around 1993, back when it was all flat text files, and my hacker group used a FILES.BBS file as an index, pointing to many hundreds of other text files, each with one vulnerability. At the time our collection was impressive;…
1 year ago -
security@ Is a Two-way Street
security@ Is a Two-way Street
More and more companies are embracing the benefits of maintaining a dedicated security team to not only help manage internal processes such as a systems development life cycle (SDLC) that may focus on security, but to also manage vulnerability reports from external parties. Some companies choose to implement bug bounty programs, and some do not. The manner in which they implement such programs,…
Notes: 1 / 1 year ago -
Let’s Talk About 0-days
Let’s Talk About 0-days
[This was a first draft of an article to be published on the Flashpoint Threat Intel blog. Ultimately, parts of it were adopted for a different blog but the original remains considerably different. Curtis Kang contributed significantly to the finished blog below.]
Zero-days (0-days and other variations) are exploitable vulnerabilities that the general public is unaware of—often being known by…1 year ago